

Knowledge is power and always good to share, especially when you know that sharing is caring. “Education is a key to life and no one can take it away from you” BUT .....
Some people think it is in the heart, others have thought it's in the brain. The heart still beats on it's own for a couple minutes after it is separated from the body, and the brain lives for 10 minutes after the heart stops beating and the body is clinically dead. They both contain life, and can live separate from each other for a limited amount of time. seems like "The soul" doesn't have one seat in the body, but rather is distributed evenly throughout the entire body.
But if I had a soul, I would like to think of it being located "everywhere", even outside of myself.
& ....... it doesn't always indicate Intelligence.

I am tired of hearing this Malaysian Political Drama. News online and printed showing all the same topic in frontpage, and most of it no other headlines other than Politic. Both Opposition and non-Opposition are both the same. Switch on TV "I just involve in money politics, not bribery", Internet "We are going to take down the current Govt on this date!" , SMS : YB had just got his Second Wife, Thanks for the strong support.
And I am damn tired and sleepy, till wanted to vomit blood hearing all these news in regards to politics.
They never think about us the Rakyat, just them only. All YB's the same, first they give you promise, then they go and get SECOND WIFE!
SSH Proxy Command -- connect.c
connect.c is the simple relaying command to make network connection via SOCKS and https proxy. It is mainly intended to be used as proxy command of OpenSSH. You can make SSH session beyond the firewall with this command,
Features of connect.c are:
- Supports SOCKS (version 4/4a/5) and https CONNECT method.
- Supports NO-AUTH and USERPASS authentication of SOCKS
- You can input password from tty, ssh-askpass or environment variable.
- Run on UNIX or Windows platform.
- You can compile with various C compiler (cc, gcc, Visual C, Borland C. etc.)
- Simple and general program independent from OpenSSH.
- You can also relay local socket stream instead of standard I/O.
Download source code from: http://www.taiyo.co.jp/~gotoh/ssh/connect.c
For windows user, pre-compiled binary is also available: http://www.taiyo.co.jp/~gotoh/ssh/connect.exe (compiled with MSVC)
What is 'proxy command'
OpenSSH development team decides to stop supporting SOCKS and any other tunneling mechanism. It was aimed to separate complexity to support various mechanism of proxying from core code. And they recommends more flexible mechanism: ProxyCommand option instead.
Proxy command mechanism is delegation of network stream communication. If ProxyCommand options is specified, SSH invoke specified external command and talk with standard I/O of thid command. Invoked command undertakes network communication with relaying to/from standard input/output including iniitial communication or negotiation for proxying. Thus, ssh can split out proxying code into external command.
The connect.c program was made for this purpose.
How to Use
Get Source
Download source code from here.
If you are MS Windows user, you can get pre-compiled binary from here.
Compile and Install
In most environment, you can compile connect.c simply. On UNIX environment, you can use cc or gcc. On Windows environment, you can use Microsoft Visual C, Borland C or Cygwin gcc.
| Compiler | command line to compile |
|---|---|
| UNIX cc | cc connect.c -o connect |
| UNIX gcc | gcc connect.c -o connect |
| Solaris | gcc connect.c -o connect -lnsl -lsocket -lresolv |
| Microsoft Visual C/C++ | cl connect.c wsock32.lib advapi32.lib |
| Borland C | bcc32 connect.c wsock32.lib advapi32.lib |
| Cygwin gcc | gcc connect.c -o connect |
| Mac OS/Darwin | gcc connect.c -o connect -lresolv |
To install connect command, simply copy compiled binary to directory in your PATH (ex. /usr/local/bin). Like this:
$ cp connect /usr/local/bin
Modify your ~/.ssh/config
Modify your ~/.ssh/config file to use connect command as proxy command. For the case of SOCKS server is running on firewall host socks.local.net with port 1080, you can add ProxyCommand option in ~/.ssh/config, like this:
Host remote.outside.net
ProxyCommand connect -S socks.local.net %h %p
%h and %p will be replaced on invoking proxy command with target hostname and port specified to SSH command.
If you hate writing many entries of remote hosts, following example may help you.
## Outside of the firewall, use connect command with SOCKS conenction.
Host *
ProxyCommand connect -S socks.local.net %h %p
## Inside of the firewall, use connect command with direct connection.
Host *.local.net
ProxyCommand connect %h %p
If you want to use http proxy, use -H option instead of -S option in examle above, like this:
## Outside of the firewall, with HTTP proxy
Host *
ProxyCommand connect -H proxy.local.net:8080 %h %p
## Inside of the firewall, direct
Host *.local.net
ProxyCommand connect %h %p
Use SSH
After editing your ~/.ssh/config file, you are ready to use ssh. You can execute ssh without any special options as if remote host is IP reachable host. Following is an example to execute hostname command on host remote.outside.net.
$ ssh remote.outside.net hostname
remote.outside.net
$
Have trouble?
If you have trouble, execute connect command from command line with -d option to see what is happened. Some debug message may appear and reports progress. This information may tell you what is wrong. In this example, error has occurred on authentication stage of SOCKS5 protocol.
$ connect -d -S socks.local.net unknown.remote.outside.net 110
DEBUG: relay_method = SOCKS (2)
DEBUG: relay_host=socks.local.net
DEBUG: relay_port=1080
DEBUG: relay_user=gotoh
DEBUG: socks_version=5
DEBUG: socks_resolve=REMOTE (2)
DEBUG: local_type=stdio
DEBUG: dest_host=unknown.remote.outside.net
DEBUG: dest_port=110
DEBUG: Program is $Revision: 1.20 $
DEBUG: connecting to xxx.xxx.xxx.xxx:1080
DEBUG: begin_socks_relay()
DEBUG: atomic_out() [4 bytes]
DEBUG: >>> 05 02 00 02
DEBUG: atomic_in() [2 bytes]
DEBUG: <<< 05 02
DEBUG: auth method: USERPASS
DEBUG: atomic_out() [some bytes]
DEBUG: >>> xx xx xx xx ...
DEBUG: atomic_in() [2 bytes]
DEBUG: <<< 01 01
ERROR: Authentication faield.
FATAL: failed to begin relaying via SOCKS.
More Detail
Command line usage is here:
usage: connect [-dnhs45] [-R resolve] [-p local-port] [-w sec]
[-H [user@]proxy-server[:port]]
[-S [user@]socks-server[:port]]
host port
host and port is target hostname and port-number to connect.
-H option specify hostname and port number of http proxy server to relay. If port is omitted, 80 is used. You can specify this value by environment variable HTTP_PROXY and give -h option to use it.
-S option specify hostname and port number of SOCKS server to relay. Like -H option, port number can be omit and default is 1080. You can also specify this value pair by environment variable SOCKS5_SERVER and give -s option to use it.
-4 and -5 is for specifying SOCKS protocol version. It is valid only using with -s or -S. Default is -5 (protocol version 5)
-R is for specifying method to resolve hostname. 3 keywords (local, remote, both) or dot-notation IP address is allowed. Keyword both means; "Try local first, then remote". If dot-notation IP address is specified, use this host as nameserver (UNIX only). Default is remote for SOCKS5 or local for others. On SOCKS4 protocol, remote resolving method (remote and both) use protocol version 4a.
The -p option will forward a local TCP port instead of using the standard input and output.
The -w option specifys timeout seconds for making connection with TARGET host.
The -a option specifiys user intended authentication methods separated by comma. Currently userpass and none are supported. Default is userpass. You can also specifying this parameter by the environment variable SOCKS5_AUTH.
The -d option is used for debug. If you fail to connect, use this and check request to and response from server.
You can omit port argument when program name is special format containing port number itself. For example,
$ ln -s connect connect-25
$ ./connect-25 smtphost.outside.net
220 smtphost.outside.net ESMTP Sendmail
QUIT
221 2.0.0 smtphost.remote.net closing connection
$
This example means that the command name "connect-25" contains port number 25 so you can omit 2nd argument (and used if specified explicitly).
Specifying user name via environment variables
There are 5 environemnt variables to specify user name without command line option. This mechanism is usefull for the user who using another user name different from system account.
- SOCKS5_USER
- Used for SOCKS v5 access.
- SOCKS4_USER
- Used for SOCKS v4 access.
- SOCKS_USER
- Used for SOCKS v5 or v4 access and varaibles above are not defined.
- HTTP_PROXY_USER
- Used for HTTP proxy access.
- CONNECT_USER
- Used for all type of access if all above are not defined.
Following table describes how user name is determined. Left most number is order to check. If variable is not defined, check next variable, and so on.
| SOCKS v5 | SOCKS v4 | HTTP proxy | |
|---|---|---|---|
| 1 | SOCKS5_USER | SOCKS4_USER | HTTP_PROXY_USER |
| 2 | SOCKS_USER | ||
| 3 | CONNECT_USER | ||
| 4 | (query user name to system) | ||
Specifying password via environment variables
There are 5 environemnt variables to specify password. If you use this feature, please note that it is not secure way.
- SOCKS5_PASSWD
- Used for SOCKS v5 access. This variables is compatible with NEC SOCKS implementation.
- SOCKS5_PASSWORD
- Used for SOCKS v5 access if SOCKS5_PASSWD is not defined.
- SOCKS_PASSWORD
- Used for SOCKS v5 (or v4) access all above is not defined.
- HTTP_PROXY_PASSWORD
- Used for HTTP proxy access.
- CONNECT_PASSWORD
- Used for all type of access if all above are not defined.
Following table describes how password is determined. Left most number is order to check. If variable is not defined, check next variable, and so on. Finally ask to user interactively using external program or tty input.
| SOCKS v5 | HTTP proxy | |
|---|---|---|
| 1 | SOCKS5_PASSWD | HTTP_PROXY_PASSWORD |
| 2 | SOCKS_PASSWORD | |
| 3 | CONNECT_PASSWORD | |
| 4 | (ask to user interactively) | |
Limitations
SOCKS5 authentication
Only NO-AUTH and USER/PASSWORD authentications are supported. GSSAPI authentication (RFC 1961) and other draft authentications (CHAP, EAP, MAF, etc.) is not supported.
HTTP authentication
BASIC authentication is supported but DIGEST authentication is not.
Switching proxy server
There is no mechanism to switch proxy server regarding to PC environment. This limitation might be bad news for mobile user. Since I do not want to make this program complex, I do not want to support although this feature is already requested. Please advice me if there is good idea of detecting environment to swich and simple way to specify conditioned directive of servers.
One tricky workaround exists. It is replacing ~/.ssh/config file by script on ppp up/down.
There's another example of wrapper script (contributed by Darren Tucker). This script costs executing ifconfig and grep to detect current environment, but it works. (NOTE: you should modify addresses if you use it.)
#!/bin/sh
## ~/bin/myconnect --- Proxy server switching wrapper
if ifconfig eth0 |grep "inet addr:192\.168\.1" >/dev/null; then
opts="-S 192.168.1.1:1080"
elif ifconfig eth0 |grep "inet addr:10\." >/dev/null; then
opts="-H 10.1.1.1:80"
else
opts="-s"
fi
exec /usr/local/bin/connect $opts $@
Tips
Proxying socket connection
In usual, connect.c relays network connection to/from standard input/output. By specifying -p option, however, connect.c relays local network stream instead of standard input/output. With this option, connect command waits connection from other program, then start relaying between both network stream.
This feature may be useful for the program which is hard to SOCKSify.
Use with ssh-askpass command
connect.c ask you password when authentication is required. If you are using on tty/pty terminal, connect can input from terminal with prompt. But you can also use ssh-askpass program to input password. If you are graphical environment like X Window or MS Windows, and program does not have tty/pty, and environment variable SSH_ASKPASS is specified, then connect.c invoke command specified by environment variable SSH_ASKPASS to input password. ssh-askpass program might be installed if you are using OpenSSH on UNIX environment. On Windows environment, pre-compiled binary is available from here.
This feature is limited on window system environment.
And also useful on Emacs on MS Windows (NT Emacs or Meadow). It is hard to send passphrase to connect command (and also ssh) because external command is invoked on hidden terminal and do I/O with this terminal. Using ssh-askpass avoids this problem.
Use for Network Stream of Emacs
Although connect.c is made for OpenSSH, it is generic and independent from OpenSSH. So we can use this for other purpose. For example, you can use this command in Emacs to open network connection with remote host over the firewall via SOCKS or HTTP proxy without SOCKSifying Emacs itself.
There is sample code: http://www.taiyo.co.jp/~gotoh/lisp/relay.el
With this code, you can use relay-open-network-stream function instead of open-network-stream to make network connection. See top comments of source for more detail.
Remote resolver
If you are SOCKS4 user on UNIX environment, you might want specify nameserver to resolve remote hostname. You can do it specifying -R option followed by IP address of resolver.
Hopping Connection via SSH
Conbination of ssh and connect command have more interesting usage. Following command makes indirect connection to host2:port from your current host via host1.
ssh host1 connect host2 port
This method is useful for the situations like:
- You are outside of organizasion now, but you want to access an internal host barriered by firewall.
- You want to use some service which is allowed only from some limited hosts.
For example, I want to use local NetNews service in my office from home. I cannot make NNTP session directly because NNTP host is barriered by firewall. Fortunately, I have ssh account on internal host and allowed using SOCKS5 on firewall from outside. So I use following command to connect to NNTP service.
$ ssh host1 connect news 119
200 news.my-office.com InterNetNews NNRP server INN 2.3.2 ready (posting ok).
quit
205 .
$
By combinating hopping connection and relay.el, I can read NetNews using Wanderlust on Emacs at home.
|
External (internet) | Internal (office)
|
+------+ +----------+ +-------+ +-----------+
| HOME | | firewall | | host1 | | NNTP host |
+------+ +----------+ +-------+ +-----------+
emacs <-------------- ssh ---------------> sshd <-- connect --> nntpd
<-- connect --> socksd <-- SOCKS -->
As an advanced example, you can use SSH hopping as fetchmail's plug-in program to access via secure tunnel. This method requires that connect program is insatalled on remote host. There's example of .fetchmailrc bellow. When fetchmail access to mail-server, you will login to remote host using SSH then execute connect program on remote host to relay conversation with pop server. Thus fetchmail can retrieve mails in secure.
poll mail-server protocol pop3 plugin "ssh %h connect localhost %p" username "username" password "password"
Break The More Restricted Wall
If firewall does not provide SOCKS nor HTTPS other than port 443, you cannot break the wall in usual way. But if you have you own host which is accessible from internet, you can make ssh connection to your own host by configuring sshd as waiting at port 443 instead of standard 22. By this, you can login to your own host via port 443. Once you have logged-in to extenal home machine, you can execute connect as second hop to make connection from your own host to final target host, like this:
$ cat ~/.ssh/config Host home ProxyCommand connect -H firewall:8080 %h 443
Host server ProxyCommand ssh home connect %h %p ... internal$ ssh home You are logged in to home! home# exit internal$ ssh server You are logged in to server! server# exit internal$
This way is similar to "Hopping connection via SSH" except configuring outer sshd as waiting at port 443 (https). This means that you have a capability to break the strongly restricted wall if you have own host out side of the wall.
|
Internal (office) | External (internet)
|
+--------+ +----------+ +------+ +--------+
| office | | firewall | | home | | server |
+--------+ +----------+ +------+ +--------+
<------------------ ssh --------------------->sshd:443
<-- connect --> http-proxy <-- https:443 --> any
connect <-- tcp --> port
NOTE: If you wanna use this, you should give up hosting https service at port 443 on you external host 'home'.
F.Y.I.
Difference between SOCKS versions.
SOCKS version 4 is first popular implementation which is documented here. Since this protocol provide IP address based requesting, client program should resolve name of outer host by itself. Version 4a (documented here) is enhanced to allow request by hostname instead of IP address.
SOCKS version 5 is re-designed protocol stands on experience of version 4 and 4a. There is no compativility with previous versions. Instead, there's some improvement: IPv6 support, request by hostname, UDP proxying, etc.
Configuration to use HTTPS
Many http proxy servers implementation supports https CONNECT method (SLL). You might add configuration to allow using https. For the example of DeleGate ( DeleGate is a multi-purpose application level gateway, or a proxy server) , you should add https to REMITTABLE parameter to allow HTTP-Proxy like this:
delegated -Pxxxx ...... REMITTABLE='+,https' ...
For the case of Squid, you should allow target ports via https by ACL, and so on.
SOCKS5 Servers
- NEC SOCKS Reference Implementation
- Reference implementation of SOKCS server and library.
- Dante
- Dante is free implementation of SOKCS server and library. Many enhancements and modulalized.
- DeleGate
- DeleGate is multi function proxy service provider. DeleGate 5.x.x or earlier can be SOCKS4 server, and 6.x.x can be SOCKS5 and SOCKS4 server. and 7.7.0 or later can be SOCKS5 and SOCKS4a server.
Specifications
- socks4.protocol.txt
- SOCKS: A protocol for TCP proxy across firewalls
- socks4a.protocol.txt
- SOCKS 4A: A Simple Extension to SOCKS 4 Protocol
- RFC 1928
- SOCKS Protocol Version 5
- RFC 1929
- Username/Password Authentication for SOCKS V5
- RFC 2616
- Hypertext Transfer Protocol -- HTTP/1.1
- RFC 2617
- HTTP Authentication: Basic and Digest Access Authentication
Related Links
Similars
- Proxy Tunnel -- Proxying command using https CONNECT.
- stunnel -- Proxy through an https tunnel (Perl script)
$ for fl in YOURMOVFILE.MOV
do
mencoder ${fl} -o ${fl/mov/avi} -oac mp3lame -ovc lavc
mplayer -ao pcm -vo null -vc dummy -dumpaudio -dumpfile ${fl/mov/mp3} ${fl/mov/avi}
#rm ${fl/mov/avi}
done
Output
Of course, you need mplayer and mencoder installed.
ffmpeg is perfectly up to this task as well, although I think mencoder is a little faster. The syntax that I have been using (specifying a 60FPS frame rate) is the following:
$ ffmpeg -i file-name.mov -g 60 -vcodec msmpeg4v2 -acodec pcm_u8 file-name.avi
This works a charm and really shrinks the file size. My original 17 second clip in its original .mov file format weighed in at 8.5MB. Following conversion the avi clip weighed in at 855.5KB.
Of course, the conversion has a degenerative affect on playback, towit, it might look pretty bad stacked up against the original, but that's what you get. If you know a better way, or better ffmpeg conversion syntax, then hook us all up.
(1) Install MediaWiki (the example given here is done by login as root and type the command in terminal mode)
# yum install mediawiki
Normally, yum would also install php-mysql, php-pgsql, php, httpd because they are dependencies.
(2) Apache (httpd) needs the file /etc/mime.types which is provided by the package mailcap. But when install httpd, yum does not know that httpd needs mailcap, so you have to install mailcap manually.
# yum install mailcap
(3) MediaWiki requires a database server. Since the database server can be MySQL or PostgreSQL, and it does not have to be on the same computer, the database server is not defined as a dependency for mediawiki.
If you want to use MySQL
# yum install mysql-server mysql
If you want to use PostgreSQL
# yum install postgresql-server postgresql
(4) Start database server (if using MySQL) and web server
# service mysql start
# service httpd start
If you want to automatically start them every time you reboot the system, type the following commands
# chkconfig mysql on
# chkconfig httpd on
(5) MediaWiki is installed in /usr/share/mediawiki with files specific to a site installed in /var/www/wiki which contains the following directories and files
config/
config/index.php
images/
index.php -> /usr/share/mediawiki/index.php
The files in /var/www/wiki is used as a template. Without making any customizations in Apache (httpd.conf), Apache can only access /var/www/html. So copy the MediaWiki template directory to /var/www/html
# cp -a /var/www/wiki /var/www/html
Now the files for your wiki is in /var/www/html/wiki and your wiki pages are stored in database server (to be installed later)
(6) The files which define the skins for the wiki (images, css, js) is installed in /usr/share/mediawiki/skins which is not accessible by web server. You have to make them accessible by one of the following ways.
If you would not make any customization to the skins, create a soft link to the skins directory
# ln -s /usr/share/mediawiki/skins /var/www/html/wiki/skins
If you would customize the skins, copy the skins directory
# cp -a /usr/share/mediawiki/skins /var/www/html/wiki
(7) Enter the following URL in your web browser (Firefox, or Konqueror, or any of your favourite)
http://localhost/wiki
(8) For first time access to MediaWiki, it would response with a page saying "Please set up the wiki first." Click on the link, which would browse to
http://localhost/wiki/config/index.php
(9) Fill in the options in the configuration page. Most of them just accept the default will be OK. Remember to choose either MySQL or PostreSQL as your database server. I suggest click on the "Use superuser account" checkbox, and enter the username of the database superuser account and password (For MySQL, the default superuser is root, for PostgreSQL, it is postgres), otherwise it may have problems in creating the database.
(10) Click the "Install MediaWiki" button at the bottom of the configuration page.
(11) If everything is OK, "MediaWiki installation successful" page is displayed.
(12) Move the config/LocalSettings.php file into the parent directory, e.g. in terminal command mode,
# mv /var/www/html/wiki/config/LocalSettings.php /var/www/html/wiki
(13) Remove the config directory for security reason
# rm -fr /var/www/html/wiki/config
(14) Type the following URL in your web browser, firefox or konquerer, or any others
http://localhost/wiki
(15) The MediaWiki main page should be displayed.
Hope this can help. Further enhancements are welcome. Where is the VOBS!
Welcome to Fedora 11 |
For more general information about the Fedora Project, including goals, values, how to get Fedora, and how to join the global community of contributors, see the Overview page.
Comprehensive release notes for Fedora 11 are also available, which describe the changes in Fedora since the last release, and are full of information for both new and experienced users.
Download Fedora 11
To get a copy of Fedora 11, visit get.fedoraproject.org. Options for direct download and BitTorrent are available.
Fedora 11 Release Overview
Fedora 11 continues the Fedora Project's tradition of the Four Foundations: Freedom, Friends, Features, First. Freedom represents dedication to free software and content. Friends represents the strength of our community. Features represents our commitment to excellence. First represents our commitment to innovation.
Fedora's hallmarks are technical excellence and innovation. Fedora 11 is packed with tons of new features across the spectrum from casual desktop user to hardcore hacker. Additionally, Fedora 11 offers a very good technical preview of features that may appear in the upcoming version of Red Hat Enterprise Linux. Fedora 11 showcases a new default filesystem in ext4, a 20 second startup, and the latest GNOME, KDE and XFCE releases. Firefox 3.5 and Thunderbird 3 latest pre-releases are available as well. Fedora 11 features Presto, a yum plugin that reduces bandwidth consumption drastically by downloading only binary differences between updates. It also features Openchange for interoperability with Microsoft Exchange. There are new security enhancements, improved and upgraded development tools, and cutting edge features in areas such as virtualization.
For a complete list of Fedora 11 features see the complete Fedora 11 feature list.
For some more detailed coverage of features, you can see either the Fedora 11 talking points for a high level overview or take a look at the Fedora 11 in-depth feature profiles for more detailed discussion on specific features.
Screenshot Tour
The Fedora 11 screenshot tour includes what's new and exciting in pictorial form. Enjoy the new KDE 4.2.2, Firefox 3.5,Thunderbird 3 or the new PulseAudio volume controls.
Fedora 11 Multimedia
In anticipation of the release there have been several podcasts and interviews produced as well as other multimedia such as screencasts. You can find links to those below.
Podcasts
A number of podcasts on topics such as a General Overview of F11 and specific features like Presto, Kernel Mode Setting, and PackageKit can be found at the Fedora 11 podcasts page.
Print Interviews
An interview with Lennart Poettring on Fedora 11's Volume Control - The Sound of Fedora 11
An interview with Daniel Berrange on upcoming Virtualization improvements in Fedora 11 - Fedora 11: Virtual(ization) Reality
An interview with Bastien Nocera on Fedora 11's Fingerprint Authentication - Fedora 11: Raise Thy Mighty...Finger?
Screencasts
Plymouth (Fedora's graphical boot system) includes a new bootup sequence called "Charge," created by Mike Langlie and Ray Strode. Plymouth has a separate plugin system that allows anyone to create themes such as "Charge" for use on Fedora or other derivative distributions.
 |
| Ogg-Theora Video |
You can watch this video directly within Firefox 3.1 or higher, such as in Firefox 3.5 provided by Fedora 11, or other HTML 5 capable browsers. Using a different browser that's not HTML 5 capable? You have our sympathies. Try these links:
****************************************************************************Fedora 11 Upgrade Tutorial
I've already got Fedora 10 and want to upgrade to Fedora 11. How do I upgrade my computer from Fedora Linux 10 to Fedora Linux 11?
Fedora 11 can be directly upgraded over the Internet using the various methods available. Backup all your data (/home and other directories), config file and sql files. Use tools such as rsync or tar to make backup to CD / DVD or other server.
Login as root user to perform upgrade.
 WARNING! It is not possible to upgrade directly from Fedora 9 to Fedora 11. To upgrade Fedora 9 to Fedora 11, upgrade to Fedora 10 first. Make sure you backup imporant data before using the information provided below. Also, the yum update step should NOT be run inside a gnome / kdep desktop session/gnome-terminal. It could result in a unusable install when gnome-terminal segfaults during the upgrade. Update should be run in a vty, runlevel 3, or a screen session.
WARNING! It is not possible to upgrade directly from Fedora 9 to Fedora 11. To upgrade Fedora 9 to Fedora 11, upgrade to Fedora 10 first. Make sure you backup imporant data before using the information provided below. Also, the yum update step should NOT be run inside a gnome / kdep desktop session/gnome-terminal. It could result in a unusable install when gnome-terminal segfaults during the upgrade. Update should be run in a vty, runlevel 3, or a screen session. Apply Fedora 10 Patches and Software Updates
Type the following command to apply existing update:# yum update rpmReboot the system if a new kernel installed for Fedora 10 (otherwise skip to next step):
# yum -y update
# yum clean all# reboot
Upgrade Fedora 10 to Fedora 11
Type the following commands to perform actual upgrade:# yum install preupgrade
# preupgrade
If you need GUI tool, enter:# preupgrade-gui
How do I Upgrade Fedora 10 Server?
Backup everything and type the following commands as root user:# yum -y update
# yum install preupgrade
# preupgrade-cli
# reboot
How Do I Upgrade Fedora 10 Using CD / DVD?
Apply existing patches to fedora 10:# yum -y update
Backup all required data, config and sql files.
Insert CD / DVD into CDROM and reboot the system. Make sure BIOS is configured to boot from CD / DVD.
To perform an upgrade, select Perform an upgrade of an existing installation. Click Next when you are ready to begin your upgrade.
This article I copied for my personal reference since I tend to forget things such as names, addresses, SSH Tunnel configurations, severe acts of nature and so on…
Concerning Tunnels:
A tunnel is usually an underground passage from one place to another. Why is there a reason to go through a tunnel instead above ground I can’t really answer in general, but I sure know why I have to use tunnels in my daily IT routines.
The tunneling allows me to deliver payload securely and also allows me to access resources that are otherwise restricted from my location.
The example below demonstrates the setup of an SSH Tunnel that is used for simple internet browsing.
Microsoft Windows 2000/XP/2003/Vista
When using Microsoft Windows operating systems I create SSH Tunnels using Putty.
1. Connect to an SSH server using Putty.
In this example I am using the hosting for this website.
2. Right click on the SSH Toolbar and select “Change Settings…”
3. On the newly opened windows select Connection >> SSH >> Tunnels. Type in the source port the number “80″. This number is simply an example and you must feel free to use any appropriate port number on your host.
In the destination text box type “localhost” and select the radio button “Dynamic”.
4. Click Add and add other ports if you might need them for some purpose. You should see your Port forwarding rule added as D80 if you have used the above settings. Once you added the port forwarding, apply the change.
Your tunnel is now ready. You can check this with telnet for example.
Linux/Mac OSX/UNIX
Under Linux the configuration is quite simplified compared to windows so no screen shots are neccessary.
Open a terminal and connect to the remote ssh server/host with the following command:
host# sudo /sbin/ssh -p22 -D 80 user@unix.soteks.com
Follows the browser configuration. It is similar config in most operating systems and browsers.
5. In Mozilla (quite similar in IE) open the Options or Properties of the browser. Navigate to Network and select Settings.
6. Select Manual Proxy configuration. Under the SOCKS Host type localhost and for port number put 80. Select SOCKS v.5. Click OK.
Once the above is completed successfully. All of your firefox traffic is being tunneled through the ssh connection that you have done so all the traffic is encrypted.
In addition to such setup I usually use the extra feature to forward by DNS requests through the tunnel too. This is a good idea if your DNS queries are being logged. To do this simply type about:config in the address bar of Firefox and in the filter line search for dns. Find the value network.proxy.socks_remote_dns and change the value to true.
7. In the address tab of firefox type about:config. In the Filter box search for DNS
It is considered a crime to use the above to get to your Friendface websites.
Enjoy.
It’s about 3:45 pm and you’ve just beaten your old Tetris high score. The end of the work day is within sight, with little over an hour to go. Suddenly, your middle-management of a boss rolls into your office. It seems the guys down in IT taddled on you. “newgrounds.com? wildbestiality.com? Gamer Gaiden? These are not resources pertinent to your duties with this company.” Busted. Maybe you should’ve made monster.com a hit on your list, because the unemployment line doesn’t offer a T1 line to pass the time.
Today’s little soiree is dedicated to misuse of company resources. I’ve had a few jobs in my time, both back-breaking and lazy. The most money I’ve ever been paid are by people who want what I know, not what I do. Since that’s not as much as people think, I rarely spend 40 hours a week dedicated to productive work. When one sits in an office, one has a computer, and often an Internet connection. Human nature dictates that such resources be used for chatting, porn, and flash games. Companies know this. However, they want you to use this time productively. We have a conflict of interests. If you aren’t being outright blocked, you probably at least have someone who is paid more then you to sit on the Internet, chatting, watching porn, and playing flash games, who will occasionally look up what you’ve been doing and tell your boss.
These articles here are going to be about setting yourself up with a little privacy. Article one is about a tool called a tunnel, which sends data from point A to point B without anyone inbetween being able to make out what it says. All they know is that “something” is going to point B. Ideally, point B is an area you control, not the geeks down the hall, and so they can’t check up on or control it. From point B, the data rushes off into the internet like little fairies on mushrooms, as is the natural state of data. You will need a point B, being a SSH server that you can log into. This article doesn’t cover setting up the server. You’ll have to wait on that, or hit up the wide internet. I have one running on my router at home.
- You’ll need to download PuTTY. Just the putty.exe file is plenty. It doesn’t require installing, so you don’t need administrator rights on your machine to run it. Save that somewhere out of the way, perhaps on a thumbdrive or somewhere not right on your Desktop in plain view.
- Open Notepad, and create a one-line batch file:
putty -D 8080 -P p# -ssh ip# - Replace p# with the port number of your SSH server and ip# with the IP address. Save this as putty.bat in the same directory as putty.exe.
- Open your browser, and go to whatismyip.com. This number is your office’s IP, or something remotely to that effect.
- Run putty.bat. It’ll ask you for a username and password, then sit idly. After you login, your tunnel is open. You can close the tunnel at any time by typing exit.
The tunnel, by itself, isn’t going to do the job for you. Each program has to be told about the tunnel, which is done via proxy settings. They’re in different places in every program, and even in different versions of different programs. For example, in Internet Explorer 6.0, you go to the Tools menu > Internet Options. Choose the Connections tab and press LAN Settings at the bottom. Under Proxy Settings, check the box to use a proxy server. Enter the IP address as 127.0.0.1, and the port number as 8080. This basically says to use this computer as the proxy, where it’ll see your lovely tunnel, and run with it. The port 8080 was set with our “-D 8080″ part of our putty.bat file.
With your proxy settings set, again go to whatismyip.com, and check that the IP has changed. Chances are, this’ll be your SSH server you logged into, or something on its network, but more importantly, not the number it was last time you checked. This is a sign that your tunnel is in use, and your browsing habit reports are being slimmed down to “stuff’s going somewhere”.
Now, so long as they don’t get the impression you’re secretly sending company data in large quantities to your home, all should be well.
- If you find your company blocking lots of port numbers, set both the SSH server and your p# in putty.bat to something they wouldn’t block. Port 80 is used for plain web traffic, and so they can’t block it outright. Usually, though, the default of 22 isn’t blocked.
- Don’t actually use this for anything illegal. There, I said it. Last thing ol’ Axel needs is jail time. My ass is too sensitive for prison sex. As always, I’m not responsible for your stupidity. This isn’t super-level security and the big boys know how it works too.
It started back in 1957 in a radio forum held by Mr Ian Kingsley, a radio programme organiser. This generated a lot of interest among the Dayak community.
The mode of celebration varies from place to place. Preparation starts early. Tuak (rice wine) is brewed (at least one month before the celebration) and traditional delicacies like penganan (cakes from rice flour, sugar and coconut milk) are prepared. As the big day approaches, everyone will be busy with general cleaning and preparing food and cakes. On Gawai Eve, glutinous rice is steamed in bamboo (ngelulun pulut). In the longhouse, new mats will be laid out on the ruai (an open gallery which runs through the entire length of the longhouse). The walls of most bilik (rooms) and the ruai are decorated with Pua Kumbu (traditional blankets). A visit to clean the graveyard is also conducted and offerings offered to the dead. After the visit it is important to bathe before entering the longhouse to ward off bad luck.
The celebration starts on the evening of 31 May. In most Iban longhouses, it starts with a ceremony called Muai Antu Rua (to cast away the spirit of greed), signifying the non-interference of the spirit of bad luck in the celebration. Two children or men each dragging a chapan (winnowing basket) will pass each family's room. Every family will throw some unwanted article into the basket. The unwanted articles will be tossed to the ground from the end of the longhouse for the spirit of bad luck.
Around 6 pm or as the sun sets, miring (offering ceremony) will take place. Before the ceremony, gendang rayah (ritual music) is performed. The Feast Chief thanks the gods for the good harvest, and asks for guidance, blessings and long life as he waves a cockerel over the offerings. He then sacrifices the cockerel and a little blood is used together with the offerings.
Once the offering ceremony is done, dinner is then served at the ruai. Just before midnight, a procession up and down the ruai seven times called Ngalu Petara (welcoming the spirit gods) is performed. During this procession, a beauty pageant to choose the festival's queen and king (Kumang & Keling Gawai) is sometimes conducted. Meanwhile, drinks, traditional cakes and delicacies are served.
At midnight, the gong is beaten to call the celebrants to attention. The longhouse Chief (tuai rumah) or Festival Chief will lead everyone to drink the Ai Pengayu (normally tuak for long life) and at the same time wish each other "gayu-guru, gerai-nyamai" (long life, health and prosperity). The celebration now turns merrier and less formal. Some will dance to the traditional music played, others will sing the pantun (poems). In urban areas, Dayaks will organise gatherings at community centres or restaurants to celebrate the evening.
Other activities that may follow the next few days include: cock-fighting matches, and blowpipe and ngajat competitions. On this day, 1 June, homes of the Dayaks are opened to visitors and guests.
Traditionally, when guests arrive at a longhouse, they are given the ai tiki as a welcome. From time to time, guests are served tuak. This would be called nyibur temuai which literally means "watering of guests".
Christian Dayaks normally attend a church mass service to thank God for the good harvest.
Gawai Dayak celebrations may last for several days. It is also during this time of year that many Dayak weddings take place, as it is one of the rare occasions when all the members of the community return home to their ancestral longhouse.
Up till 1962, the British colonial government refused to recognise Dayak Day. Gawai Dayak was formally gazetted on 25 September 1964 as a public holiday in place of Sarawak Day. It was first celebrated on 1 June 1965 and became a symbol of unity, aspiration and hope for the Dayak community. Today, it is an integral part of Dayak social life. It is a thanksgiving day marking good harvest and a time to plan for the new farming season or activities ahead.
*******************
Sa, dua, tiga, empat, lima, enam, tuuuuuujuh!
Enda aku busong ngelangkah gunong,
Enda aku tulah ngelangkah tanah,
Enda aku danjan ngelangkah bulan,
Enda aku tumbang ngelangkah bintang!
Kaki aku udah bediri di segi besi belumpong,
Nyawa aku nyapa nyembah di klasah tikai bedong long.
Lengan kanan aku ditanggam beringan lanchum selong,
Pala aku di-bap singkap jalong jabong,
Blakang aku ditinggang seludang baju burong.
Laban aku tu ukai mungkal ukai nanjal,
Aku tu endang niti endang nali,
Baka ijok tampung penduk,
Baka rutan tampung danan,
Baka ira tampung lemba,
Baka wi tampung tali.
Pecah periuk tanah ganti periuk tani,
Padam bulan diganti matahari,
Parai orang ka tuai ganti tubuh kami,
Pambu orang ka dulu ganti kami ka dudi.
Kami tu deka ngintu gawai dayak,
Nitih ka pekat, ngimbai adat menoa Sarawak,
Ngibun durok kitai bansa,
Negi ka nama enggau ADAT IBAN di Malaysia,
Ngambika tampak rita idup bersama di mata dunya.
O….Haa!
Nya baru aku ngangkat ka kita ke lama udah timpat,
Tinggang urat sebangki api.
Tu baru aku nyungkang kita ke lama udah tumbang,
Tinggang batang tebelian wi.
Aku nyerungkai kita ke lama udah parai,
Keranjai indai imbok kedidi.
(Tu aku ngangau ka aki kami Sera Gunting,
Ke tau nemuai ngagai gensiring langit kuning.
Ngangau ka tuai benama Begeri,
Ke dulu ngajar kitai beguna ka atau babi,
Laban iya ba indai ka Dara Manis Muka.
Aku ngangau ka aki kami ke benama Sarapoh,
Tuai ke berani nyanda bunoh,
Ringka-ringka ngema benong benda menaga.
Aku ngangau ka Aki kami Pateh Ambau,
Ke datai ari Pangkalan Tabau,
Peling lanting tawang ulih menang bedagang.
Aku mega ngangau ka Gerasi Belang Pinggang,
Seduai Rukok ke Pematak Bala Nyerang.
Aku ngangau ka Petara Betie “Brauh Gumbang”,
Seduai Datu Patinggi Gurang.
Aku ngangau ka Petara Jalir, Petara Gisang,
Petara Geringu, Petara Sumbang.
Aku ngangau ka Petara Gerijih Ai Marang,
Seduai Bangkam ke ngaram ka sampan buong Rajang.
Aku ngangau ka Tindin Pimpin Bragah Ngindang,
Seduai Entingi Keti Aur Tulang.
Aku ngangau ka Rekaya Tom Tajai Ngindang,
Enggau tuai entanak benama Unggang.
Ngangau ka Petara Uyut benama Bedilang,
Petara Atin apai Saang,
Petara Sabok Apai Mang,
Orang Kaya Dana Bayang,
Enggau Chulo bejulok Tarang.
Orang ngasoh aku ngambi ngabang,
Ngambi mansang,
Ngambi makai,
Ngambi nandai !)
Kita ka ari ili datai sabuah barong,
Kita ari ulu undor sabuah buong.
Kita ari langit nilik naka rekong,
Kita ari tanah nyengok naka punggong.
Ngabang abis, ngabang lengis,
Betambit pintu, bekaling alu,
Bekaling lantai, bekesai tikai.
Aku ukai ngangau ngapa, ukai ngangau pia,
Aku mai kita ngabang, mai kita mansang,
Mai kita makai, mai kita nandai.
Aku mai piring, mai ading,
Piring penganan, piring penyaran,
Piring Arak, Piring Tuak,
Udah sedia, udah nyengenda,
Ditikai wi, tikai peradani,
Ditikai rutan, tikai bemban.
Kita ke ngabang bakanya mega,
Anang tuboh puang, tuboh sabatang,
Anang mai tuboh murus, tuboh untus,
Tang mai ubat serangkap genap,
Mai batu teruba nemu,
Mai pengaroh gembar tuboh.
Anang engkah ngapa, engkah pia,
Engkah ba piring, engkah ba ading.
Ayan ka ba tegalan,
Lengka ka ba pedara,
Sikap ka di ketupat.
Ngambi ka kena peda, kena tela,
Kena iching, kena perening.
Awak ka kena genggam, kena simpan,
Kena sandoh, kena taroh,
Kena japai kena pegai.
Enggau sampi tu,
Aku Minta kami chelap-embab,
Minta gayu-guru,
Gerai-nyamai,
Bidik-lansik,
Betuah-belimpah,
Kaya-raja,
Aku minta tulang,
Minta pandang,
Minta iching,
Minta perening.
Awak ka kami mudah bulih duit, bulih ringgit,
Bulih padi, bulih puli,
Bulih reta, bulih tengkira,
Bulih setawak, bulih menganak.
Ngambi ka kami jelai rita, manah nama,
Nuchong baka bukit Rabong menoa,
Tinggi baka langit nungkat neraja,
Terang baka pandang bulan purnama.
Nya alai dinga ka kangau anak mensia, kangau anak uda,
Minta tulong, minta sukong kita.
Selamat Ngintu Gawai Dayak 2009, Gayu Guru, Gerai Nyamai, Lantang Senang, Bulih Duit Bulih Ringgit, Kaya Raya Nguan Menoa.
Ari kami sebilik,
Paul Albert
Rh. Karak, Stengin, Lemanak
Engkilili
*** This year 2009 I have to work evening shift!
Previously, in work many years back I am more a Suse Lover. That is just for work. and for home I have been using CentOS and Ubuntu. More to CentOS. Then I move to fedora 6. And recently I have migrated to Fedora 10, and I love it. Superb! It is my core OS, and seldom Windows.
Manage to set it up as:
- Fun OS
- Server: Apache, WebCam, SSH server and also MySQL.
Will update again. Busy man here
Swine influenza (also swine flu, hog flu,[1] and pig flu[1]) refers to influenza caused by any strain of the influenza virus endemic in pigs (swine). Strains endemic in swine are called swine influenza virus (SIV).[1]
Of the three genera of human flu, two are endemic also in swine: Influenzavirus A is common and Influenzavirus C is rare.[2] Influenzavirus B has not been reported in swine. Within Influenzavirus A and Influenzavirus C, the strains endemic to swine and humans are largely distinct.
Swine flu is common in swine in the midwestern United States (and occasionally in other states), Mexico, Canada, South America, Europe (including the United Kingdom, Sweden, and Italy), Kenya, China, Japan, Taiwan, and other parts of eastern Asia.[1]
Swine flu is rare in humans. People who work with swine, especially people with intense exposures, are at risk of catching swine influenza if the swine carry a strain able to infect humans. However, these strains infrequently circulate between humans as SIV rarely mutates into a form able to pass easily from human to human. In humans, the symptoms of swine flu are similar to those of influenza and of influenza-like illness in general, namely chills, fever, sore throat, muscle pains, severe headache, coughing, weakness and general discomfort.
The 2009 flu outbreak in humans that is widely known as "swine flu" apparently is not solely due to a swine influenza virus. It is due to a new strain of influenza A virus subtype H1N1 that derives from one strain of human influenza virus, one strain of avian influenza virus, and two separate strains of swine influenza virus. The origins of this new strain are unknown, and the World Organization for Animal Health (OIE) reports that this strain has not been isolated in swine.[3] It passes with apparent ease from human to human, an ability attributed to an as-yet unidentified mutation.[4] The strain in most cases causes only mild symptoms and the infected person makes a full recovery without requiring medical attention and without the use of antiviral medicines.[5]
WHO boosts pandemic alert level to 4
Ontario probing 10-12 potential cases; P.E.I. investigating 8Last Updated: Monday, April 27, 2009 | 8:08 PM NT CBC News

More countries announced confirmed or suspected cases of the virus linked to the outbreak in Mexico on Monday. (CBC)
The World Health Organization raised its global pandemic alert to Level 4 from Level 3 on Monday, meaning the global health body feels the virus causing the swine flu outbreak can easily transmit between people.
Dr. Keiji Fukuda, the WHO’s assistant director general, confirmed the change during a briefing from Geneva following an emergency meeting of the organization.
Swine flu symptoms
People infected with the virus have symptoms that include:
- Fever.
- Cough.
- Sore throat.
- Muscle and joint pain.
- Shortness of breath.
Source: World Health Organization
Countries should focus their efforts on mitigating the effects of the virus — which the WHO has confirmed has spread to Mexico, Canada, the United States and Spain — because containment is impossible, he said.
However, Fukuda added: "A pandemic is not considered inevitable at this time."
Fukuda said the WHO doesn't recommend closing borders or restricting travel but is encouraging people who are ill to delay travel.
"The deliberations of the emergency committee and the decisions of the director general really reflect a lot of very careful and sober discussion and a number of important considerations," said Fukuda.
 Commuters in Mexico City wear surgical masks while riding the subway on Monday. Mexico's government is trying to stem the spread of a deadly strain of swine flu as a new work week begins by urging people to stay home if they have any symptoms of the virus believed to have killed more than 100 people. (Eduardo Verdugo/Associated Press)
Commuters in Mexico City wear surgical masks while riding the subway on Monday. Mexico's government is trying to stem the spread of a deadly strain of swine flu as a new work week begins by urging people to stay home if they have any symptoms of the virus believed to have killed more than 100 people. (Eduardo Verdugo/Associated Press) Despite the WHO's comments, the European Union and the U.S. have advised against non-essential travel to Mexico because of the outbreak of the virus believed to have killed dozens in Mexico. Canada was expected to issue a similar advisory.
The administration of U.S. President Barack Obama said it is already waging a vigorous campaign of prevention, unsure of the outbreak's severity or where it would show up next.
"We want to make sure that we have people where they need to be, equipment where it needs to be and, most of all, information shared at all levels," Secretary of Homeland Security Janet Napolitano told reporters Monday in Washington.
Napolitano said she is working with Canadian and Mexican officials in a "tri-national" approach to the outbreak. Canada's health minister, Leona Aglukkaq, said she has been in touch with her counterparts in Mexico and the U.S.
Mexico raises death toll
The number of confirmed cases rose Monday to 50 in the U.S., the result of further testing at a New York City school. The WHO has confirmed 26 cases in Mexico, six in Canada and one in Spain. All of the Canadian cases were mild, and the people have recovered.
The Mexican government suspects the virus was behind at least 149 deaths in Mexico, the epicentre of the outbreak, with hundreds more cases suspected.
More than 1,900 people have been hospitalized over what Mexican Health Minister José Angel Cordova Villalobos called "grave pneumonia," but 1,070 have since been released. He said health officials expect the number of new cases to rise.
Its first suspected case of swine flu was detected in the southern state of Oaxaca, Villalobos said Monday, but he added it was too early to identify the cause or geographical source.
Information contacts
The Canadian government has set up a hotline and websites for information about the swine flu virus. The number is 1-800-454-8302, and the websites are fightflu.ca, voyage.gc.ca and phac.gc.ca.
The Mexican government has also ordered all schools throughout the country closed until May 6.
The majority of the suspected deaths were between the ages of 20 and 50, Villalobos told reporters in Mexico City.
"We are investigating for confirmation on those cases to see if they are, in fact, flu cases," he said.
Spain, Scotland say flu has hit
More countries announced confirmed or suspected cases of the virus Monday.
Health officials in Britain said two cases have been confirmed in Scotland, but a Canadian woman hospitalized in Manchester, England, tested negative for swine flu. The WHO said it is still awaiting official reports from the U.K. about the Scottish cases.
Scottish Health Secretary Nicola Sturgeon said the two confirmed patients are "recovering well."
In Spain, the first patient, a young man who recently returned from Mexico, is responding well to treatment, Spanish Health Minister Trinidad Jimenez said.
Another 17 sick people are suspected of having the virus, but none of the people under observation is in serious condition, the minister told a news conference in Madrid.
"The situation is under control," Jimenez said.
Two people in Israel who recently returned from Mexico have been quarantined with flu-like symptoms, Israeli health officials said Monday.
Meanwhile, in New Zealand, Health Minister Tony Ryall said 13 people who had just returned from a school trip to Mexico and were showing flu-like symptoms were being tested for swine flu.
Pork imports banned
As more suspected cases are reported, countries around the world are taking action to try to stop the spread of the virus.
Airports in Germany, Singapore, Thailand, Japan, Indonesia, the Philippines, India and Malaysia were to begin screening all airline passengers from North America.
Russia, Hong Kong and Taiwan said visitors returning from flu-affected areas with fevers would be quarantined.
Australian Health Minister Nicola Roxon said pilots on international flights would be required to file a report noting any flu-like symptoms among passengers before being allowed to land in Australia.
China said anyone experiencing flu-like symptoms within two weeks of arrival had to report to authorities.
Several countries, including China, Russia and Ukraine, have also banned imports of pork and pork products from Mexico.
Azerbaijan banned all livestock products from North America while Indonesia and Lebanon announced they will ban most imported pork products.
The U.S. Centres for Disease Control and Prevention says people cannot get the flu by eating pork or pork products.
The term pandemic is a medical description of the way an infectious disease spreads and not an indication of its mortality rate.
Canadian health officials have said flu viruses in general kill about 4,000 people a year in Canada.
Datuk Amar Puan Sri Hajjah Laila Taib is of Polish-Russian descent. Her real name was Laila Chalecki and she married Abdul Taib Mahmud at the Adelaide Mosque by Iman Ahmad Skaka Al-Haj on Jan 13, 1959.
KUCHING, April 29 (Bernama) -- Puan Sri Laila Taib, wife of Sarawak Chief Minister Tan Sri Abdul Taib Mahmud, succumbed to cancer at their residence in Demak Jaya here today.
She died at 3.45pm.
Laila, 68, is survived by her husband, four children, including Deputy Tourism Minister Datuk Seri Sulaiman Abdul Rahman, and 15 grandchildren.
Taib's press secretary Amin Sahmat said the burial would be held at the Demak Muslim cemetery tomorrow morning.
Among the first dignitaries to pay their last respects at Demak Jaya this evening was Deputy Prime Minister Tan Sri Muhyiddin Yassin, who is currently on a two-day official visit to Sarawak, and wife, Puan Sri Norainee Abdul Rahman.
The Polish-born Laila and Taib, then pursuing his law degree, were married in Adelaide, Australia on Jan 13, 1959. Three years later, she arrived in Sarawak.
Her maiden name was Lejla Chaleck.
In paying tribute to Laila during their 50th wedding anniversary celebration here last January 13, Taib had said she was his pillar of strength and source of inspiration.
"I must acknowledge that it is not easy for any woman to be a politician's wife. Laila has played a major part in making my life very bearable," he said.
A local writer, Christina Mamora, who was commissioned to write Laila's yet-to-be published biography, 'A Story of Love and Compassion', described her as "kind and caring towards others."
"Having spent many long hours interviewing her (Laila) over the past year or so, I was very sad to think how nice and supportive she has been to me, especially in documenting stories about women, when I heard that she was sick," she told Bernama here.
In recognition of her active involvement in social work, including as Sarawak Badan Amal Dan Tenaga (SABATI) president, she was awarded the Darjah Utama Yang Amat Mulia Bintang Kenyalang, which carries the title 'Datuk Amar' in 1988.
She was also the Pertubuhan Kebajikan Islam Malaysia (Perkim) vice-president (women's committee chairman) while the setting up of the Laila Taib Cancer Charitable Trust was one of the many testimonials of her keen interest to help needy patients and see that research activities could be carried out for the people's benefit.
-- BERNAMA
When I first compared PCs and Macs around 1988, I decided that Mac users would be more efficient at Microsoft Word or drawing pictures than a PC user but the PC user would know far more about computers. This was because the Mac

Nowadays, the PC is becoming the "dumbed-down" operating

I assumed, in those thrilling days of yesteryear, that Mac users weren't as smart as PC users. Basically, if you're dumb (and have a lot of money), you use a Mac. These days I think that PC (Windows) users are the less skilled of the three user types. Each new version of Windows that emerges is smarter than the previous one, the new applications are released without some of the more sophisticated features they once brandished, and our gadgets (with the exception of cell phones) are built with a minimalist design.
This is all to our own detriment.
Think about it. If software companies continue to make smarter operating

I don't want to be in that position. I want my technical skills to remain sharp by working with an operating system that's close to the hardware. I like to configure, enhance, tinker, tweak, and build something that's better than what's handed to me.
The question doesn't mean, "Do you have the required intelligence to use Linux" but rather "Are you smart enough to make the decision to use Linux and keep that technical edge?"
Is Conficker Finally History?
Ian Paul
Apr 4, 2009 12:14 am

How big is the Conficker threat?
The general consensus seems to be that approximately 3 million computers are infected on any given day. The number 15 million gets thrown around a lot as well, but that number includes computers that were infected and then scrubbed clean of the malware. Keep in mind that the actual number of infected computers is also very hard to ascertain since security experts can only count infected Internet protocol (IP) addresses and not individual computers, according to Roel Schouwenberg, a security expert with Kaspersky labs. Since an entire company could be behind one IP, the number of infected devices remains a bit of a mystery.
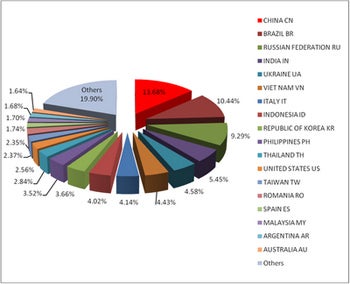
The Vietnamese security company Bkis (which offers the pie chart below, of infections by country) says approximately 2.2 million computers are currently infected with Conficker A and B, and about 1.2 million computers carry Conficker C, the latest version of the worm, according to reports. The Conficker C number is the most worrisome since that is the version that can most effectively update itself through p2p networking with no need to phone home for an update.
The world's biggest problem areas for Conficker infections are in Asia, Eastern Europe and South America, although there seems to be some disagreement on which countries are the hardest hit.
How important is Microsoft's Conficker Patch and who can get it?
Does Microsoft have the power to stop Conficker dead in its tracks? Common sense seems to say yes, because if everybody had Microsoft's Conficker patch the problem would be solved, right? Not so, says Schouwenberg. Even though Conficker-infected regions contain a high amount of computers with pirated Windows software, the blame should not be placed at Microsoft's feet.
Microsoft allows both pirate and genuine Windows users to download critical security updates. However, most pirate users have Windows' automatic updates turned off to avoid Microsoft's piracy detection tool. Pirate users could get the software from Microsoft's download center, but it's unknown how many users are actually doing that.
Another problem, Schouwenberg says, is that Internet service providers in problem regions are not as security conscious as they are in the United States. If the ISPs are not actively monitoring security on their networks and blocking the necessary ports that Conficker can sneak onto, then unpatched computers remain at risk.
But the Conficker patch and port blocking are not cure-alls. According to Schouwenburg, the security patch is most effective against Conficker A, but since Conficker has three main flavors (A, B and C), patches are not the only answer. As always, the best defense is to make sure your antivirus programs are up to date and to do a full security scan regularly. If you're worried that you might be infected, the Conficker Working Group has a simple test that can help.
If you are a pirate Windows user, you have amnesty for critical downloads so get the Conficker patch as soon as possible. Remember, we may be forgetting about the worm, but Conficker's authors still have the capability to inflict harm. Whether that will happen is anybody's guess, but making sure your computer is secure is always the best policy.
We in Batang Ai have lost a great leader, being met with him personally. Humble and down to earth type of YB and he is so friendly whenever approached. We will be missing you a lot.
May He Rest In Peace, Amen.
Taken from Bernama:
Batang Ai State Assemblyman Dies
KUCHING, Feb 24 (Bernama) -- Parti Rakyat Sarawak (PRS) vice-president Datuk Dublin Unting Ingkot passed away at the Normah Medical Specialist Centre here at about 1.25am today after suffering from a stroke.
Unting, 55, who was the Batang Ai assemblyman and sports and agriculture assistant minister, is survived by wife, Datin Froline Moriah Demies Impoi, two sons and a daughter. He had been hospitalised for the past nine months after falling into a coma following a massive stroke in May last year while being interviewed by a Radio Television Malaysia (RTM) radio channel in his capacity as the Chef de Mission for the Sarawak contingent to the Malaysian Games (Sukma).
PRS secretary-general Wilfred Nissom, who confirmed Unting's death, told Bernama that he paid him a visit last night when it was learnt that his condition had turned for the worst.
His remains will be bought back to his residence at Jalan Kampung Stutong here later today.
In the last state election held in May 2006, Unting won the predominantly Iban seat after defeating Nicholas Bawin Anggat of the Sarawak National Party (SNAP) with a 806-vote majority.
He first won the Batang Ai seat in 1991 under the Parti Bansa Dayak Sarawak (PBDS) ticket, which was then an opposition at the state level in a straight fight with Mikai Mandau from the Barisan Nasional (BN).
In the subsequent state elections held in 1996 and 2001, he retained the seat on BN-PBDS ticket and later joined PRS following PBDS deregistration due to an internal leadership crisis in 2004.
Meanwhile PRS president Datuk Seri Dr James Masing said Unting was a dedicated assemblyman who was committed to improving the socio-economic standard of his constituency and the state as a whole.
"He is a person who does not hold any grudges or ill feeling against anybody as far as I know," he told Bernama.
"On behalf of the party I offer my condolences to his family. His dedicated services to the party, constituency and state will be forever remembered," he added.
-- BERNAMA






















